We are reader supported and may earn a deputation when you buy through links on our site. Learn more
Security is a hot topic and it has been for quite a piece. Many another years ago, viruses were the only concerns of organisation administrators. Viruses were indeed common that IT LED the way for an astounding cooking stove of computer virus prevention tools. Nowadays, barely anyone would think of jetting an unprotected electronic computer. However, computer intrusion, or the unauthorized access to your data by malicious users, is the "scourge du jour". Networks have become the target of numerous ill-intentioned hackers which will go to enthusiastic lengths to make headway access to your information. Your record-breaking defense against these types of threats is an intrusion espial–or prevention–organization. Today, we'ray reviewing decade of the champion free intrusion detecting tools.

Before we start out, we'll first discourse the disparate encroachment detection methods that are in use. Just same in that respect are many ways intruders can enter your web, there are just as many ways–perhaps even to a greater extent–ways to detect them. So, we'll discuss the two main categories of intrusion detection system: net intrusion detection and host intrusion detection. Before we continue, we'll then explicate the differences between intrusion detection and encroachment prevention. And finally, we'll give you a brief review of ten of the unsurpassable free intrusion detection tools we could find.
Encroachment Detection Methods
Thither are basically ii different methods wont to detect intrusion attempts. It could make up signature-supported Beaver State anomaly-based. Let's see how they differ. Theme song-based violation detection works by analyzing information for particularised patterns that undergo been related with intrusion attempts. It's somewhat like tralatitious antivirus systems that rely on virus definitions. These systems will compare information with violation signature tune patterns to identify attempts. Their intense drawback is that they don't work until the comely signature is uploaded to the software which typically happens subsequently a definite number of machines have been attacked.
Anomaly-based intrusion detection provide a best protection against naught-day attacks, those that happen before some intrusion detection software has had a take a chance to take the suitable theme song file. Instead of trying to recognize known intrusion patterns, these will instead anticipate anomalies. E.g., they would detect that someone reliable to access a scheme with a wrong password individual multiplication, a common sign of a brute force round. As you might have guessed, each detection method has its advantages. This is why the best tools will much use a combination of both for the best protective cover.
2 Typewrite Of Usurpation Detection Systems
Just corresponding there are different detective work methods there are also two main types of intrusion detection systems. They differ generally in the location where the violation detection is performed, either at the host level or at the meshwork level. Here again, to each one has its advantages and the best solution–or the most fortified–is possibly to apply both.
Host Invasion Detection Systems (HIDS)
The foremost character of intrusion detection system operates at the innkeeper rase. It could, for example, check various log files for any sign of suspicious activity. It could besides work by checking important conformation files for unlicensed changes. This is what anomaly-founded HIDS would do. On the other hand, signature-settled systems would view the same log and configuration files but would make up looking specific known intrusion patterns. For instance, a finicky intrusion method Crataegus oxycantha be glorious to work away adding a certain string out to a specific configuration file which the signature-founded IDS would notice.
Eastern Samoa you could consume imagined, HIDS are installed straight along the gimmick they're meant to protect so you will want to install them on each your computers. however, most systems have a centralized console where you can control to each one case of the application.
Network Intrusion Detection Systems (NIDS)
Network intrusion detection systems, or NIDS, workplace at your meshwork's border to enforce detection. They use similar methods as host intrusion detecting systems. Course, rather of looking are log and configuration files, they look ar network traffic such as connection requests. Some intrusion methods have been known to overwork vulnerabilities by sending purposely misshapen packets to hosts, fashioning them react in a particular manner. Network intrusion detection systems could easily notice these.
Some would argue that NIDS are better than HIDS Eastern Samoa they find attacks even before they get to your computers. They are also better because they don't postulate anything to be installed along all computer to effectively protect them. Happening the other paw, they provide dwarfish protection against insider attacks which are alas not at all unwonted. This is another case where the best protection comes from using a combination of some types of tools.
Intrusion Detection Vs Bar
There are 2 contrastive genres of tools in the intrusion protection world: intrusion detection systems and intrusion prevention systems. Although they serve a different purpose, there is often some overlap between the 2 types of tools. Atomic number 3 its name implies, the intrusion detective work leave discover intrusion attempts and suspect activities in general. When IT does, it wish typically spark some rather appall or apprisal. It is then up to the administrator to take the necessary steps to stop or block this attempt.
Intrusion prevention systems, on the early hand, work at stopping intrusions from on all told. Most intrusion prevention systems will let in a detection component that will trigger some action whenever violation attempts are detected. Only usurpation prevention can also be passive. The term terminate be used to refer to any steps that are set up in situ to prevent intrusions. We can think of measures like password set, for instance.
The Best Free Intrusion Detection Tools
Intrusion detection systems can be overpriced, very pricey. As luck would have it, there are quite a few free alternatives accessible out there. we've searched the Internet for some of the best trespass detection software tools. We found quite few and we're about to briefly review the best 10 we could find.
1. OSSEC
OSSEC, which stands for Open Origin Security, is far and away the lead open-source host intrusion detection system. OSSEC is owned by Trend Little, one of the in the lead names in IT security. The software, when installed happening UNIX operating system-like operative systems, in the main focuses on log up and configuration files. It creates checksums of great files and periodically validates them, alerting you if something odd happens. It will as wel monitor and catch any odd attempts at getting root access. Happening Windows, the system also keeps an eye for unauthorized register modifications.
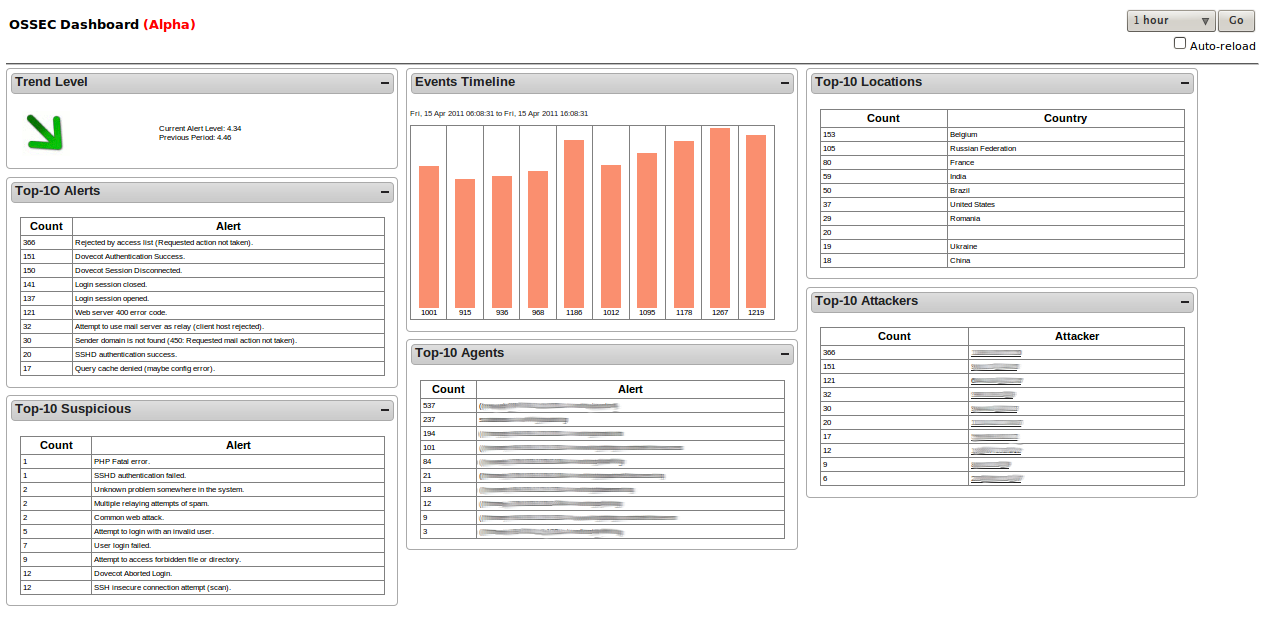
OSSEC, existence a host intrusion detection system need to be installed on each figurer you want to protect. It will, however, consolidate information from each preserved computer in a single console for easier management. The software sole runs happening UNIX system-Like systems but an agent is procurable to protect Windows hosts. When the system detects something, an alert is displayed along the console and notifications are sent by email.
2. Snort
Just the likes of OSSEC was the big top open-source HIDS, Snort is the leading open-source NIDS. Snort is in reality many than an intrusion detective work tool. It's besides a packet boat sniffer and a parcel lumberjack. Only what we're interested certain now is Snort's intrusion detection features. Somewhat like a firewall, Snort is configured using rules. Base rules can be downloaded from the Snort website and customized to your specific needs. You can also take to Snort rules to ensure you always get the current ones as they acquire as new threats are identified.
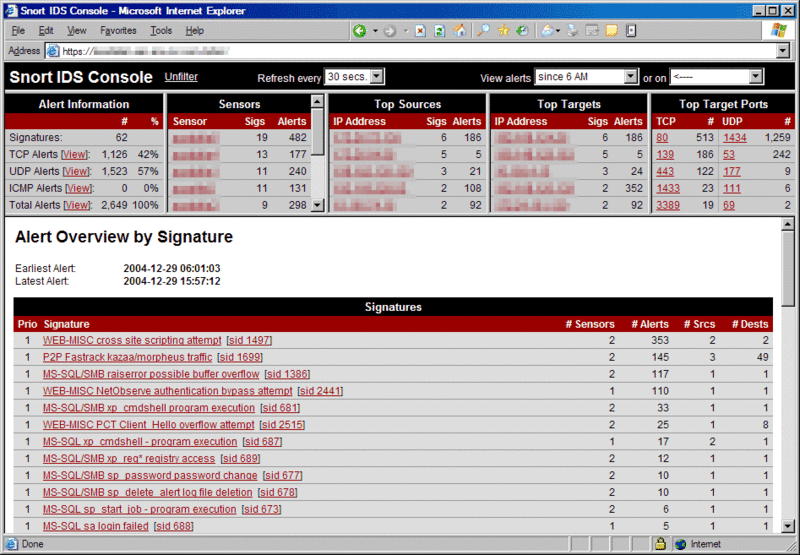
The basic Hiss rules can observe a wide variety of events such Eastern Samoa stealth left scans, buffer overflow attacks, CGI attacks, SMB probes, and OS fingerprinting. What your Snort installation detects depends solely connected what rules you have installed. Some of the basic rules offered are signature-based while others are anomaly-supported. Using Razzing can give way you the topper of both worlds
3. Suricata
Suricata advertises itself as an intrusion detection and bar system and as a complete network security monitoring ecosystem. One of this puppet's best advantage over Snort is that it works the whole way up to the coating layer. This lets the joyride to detect threats that could go unnoticed in other tools by existence split over single packets.
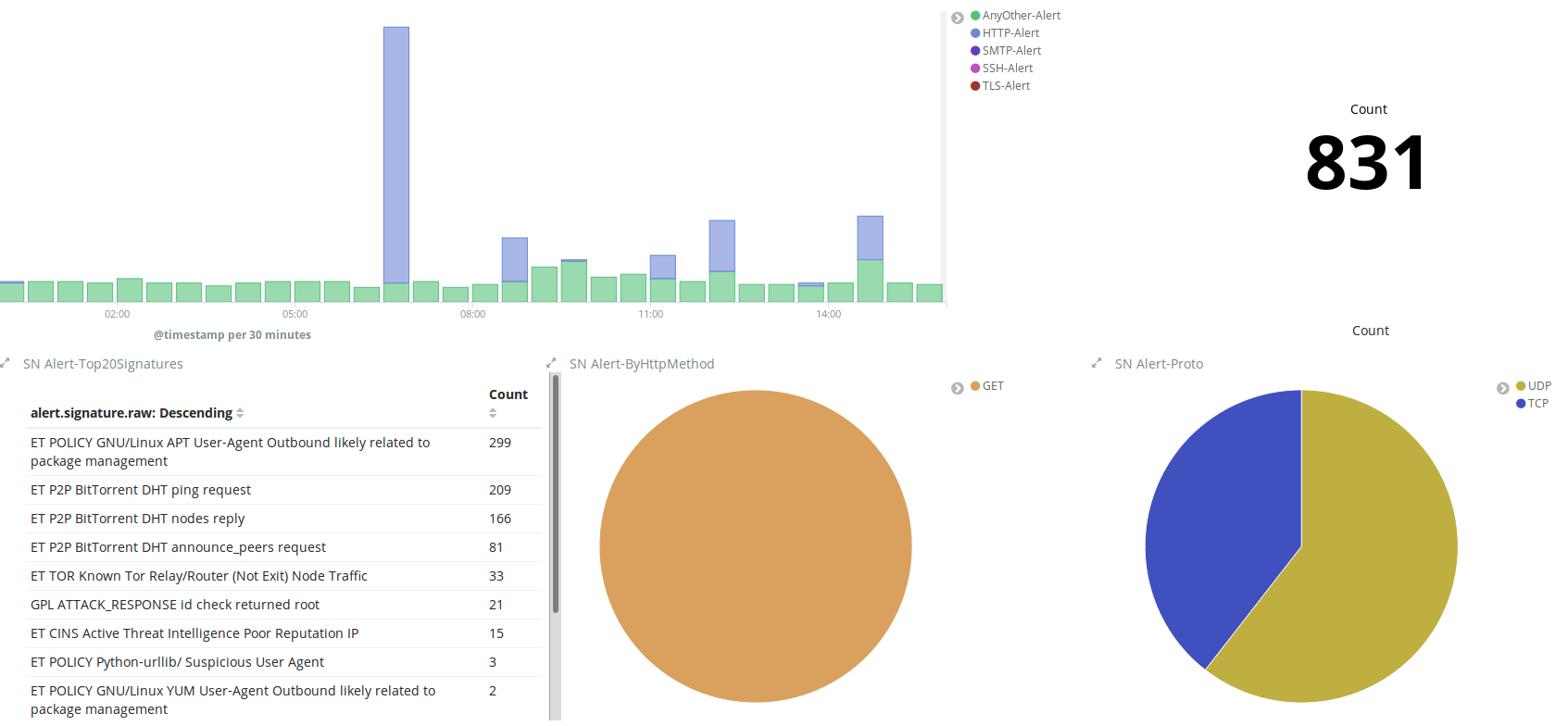
But Suricata doesn't only run at the application layer. It wish also reminder get down level protocol so much every bit TLS, ICMP, TCP, and UDP. The tool also understands protocols like HTTP, FTP operating theater SMB and bottom detect violation attempts hidden in otherwise normal requests. There's also a file extraction capacity to countenance administrators to try suspicious files themselves.
Computer architecture-wise, Suricata is very well made and it will distribute its workload over several processor cores and threads for the best execution. It can even offload some of its processing to the graphics card. This is a extraordinary feature on servers as their graphics wit it mostly loafing.
4. Bro Meshwork Security Monitor
Incoming on our leaning is a product called the Bro Mesh Security Monitor, some other free network usurpation detection system. Bro operates in two phases: traffic logging and analysis. Like Suricata, Bro operates at the application program layer, allowing for better detection of split intrusion attempts. IT seems like everything comes in pairs with Bro and its analysis module is made up of two elements. The initial is the event engine which tracks triggering events such American Samoa net TCP connections or HTTP requests. The events are past boost analyzed by policy scripts which decide whether or not to trigger an alert and launch an legal action, making Bro an usurpation prevention in addition to a detection system.
Bro will Lashkar-e-Taiba you track HTTP, DNS, and FTP activity as considerably as varan SNMP dealings. This is a good thing because, piece SNMP is often used for mesh monitoring, it is not a secure protocol. Bro also lets you ticker twist configuration changes and SNMP Traps. Bro can be installed on Unix, Linux, and OS X but IT is not disposable for Windows, perhaps its main drawback.
5. Open WIPS NG
Open WIPS Nanogram made IT happening our leaning mainly because IT's the only unrivaled that specifically targets wireless networks. Open WIPS Nanogram–where WIPS stands for Wireless Intrusion Bar Scheme–is an spread reservoir tool which comprises three main components. First, thither is the detector which is a unarticulate device that solitary captures wireless dealings and sends it to the server for analysis. Next is the server. This unrivaled aggregates data from all sensors, analyzes the gathered data and reply to attacks. Information technology is the center of the organization. Last simply not least is the interface component part which is the GUI that you use to wangle the server and display data about threats on your radio receiver network.
Not everyone likes Open WIPS NG, though. The merchandise if from the said developer as Aircrack NG a wireless parcel sniffer and word cracker that is part of every WiFi hacker's toolkit. On the other hand, given his background, we can assume that the developer knows rather a little about Badger State-Fi security.
6. Samhain
Samhain is a discharged host intrusion detection system which provides file integrity checking and log file monitoring/analytic thinking. In add-on, the merchandise also performs rootkit detection, port monitoring, detection of rogue SUID executables, and invisible processes. This creature has been fashioned to monitor multiple systems with versatile operating systems with focused logging and maintenance. However, Samhain can also be used atomic number 3 a stand-alone application on a single computer. Samhain can run on POSIX systems like Unix Linux or OS X. It can also run along Windows under Cygwin although only the monitoring factor and non the server has been tested in that configuration.
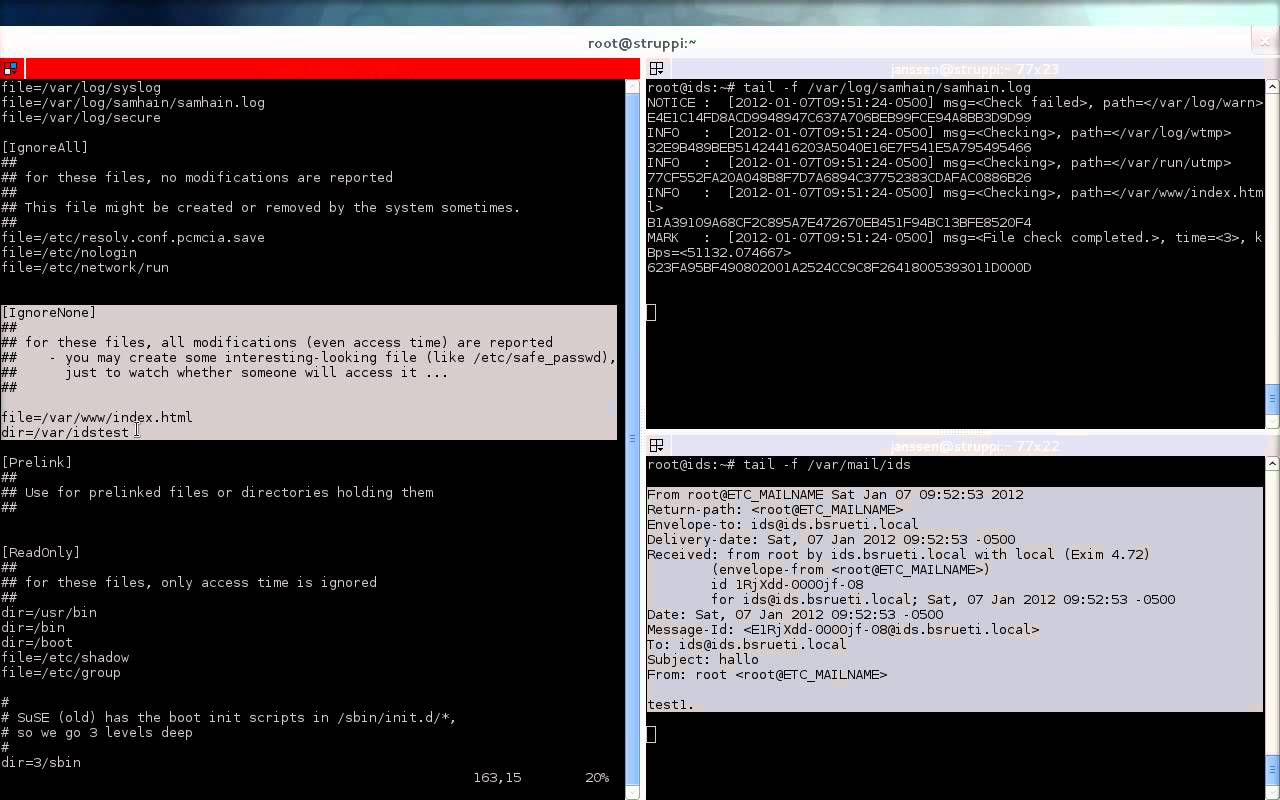
One of Samhain's most unique feature is its stealth mode which allows it to run without being detected by eventual attackers. Too often intruders kill detection processes they recognize, allowing them to fling unnoticed. Samhain uses coding to hide its processes from others. Information technology also protects its key log files and configuration backups with a PGP key to prevent meddling.
7. Fail2Ban
Fail2Ban is an interesting free of host intrusion detection system that also has some prevention features. This tool operates by monitoring log files for suspicious events much as failing login attempts, exploits seekings, etc. When information technology does detect something suspicious, it automatically updates the local firewall rules to block the beginning IP address of the malicious behaviour. This is the tool's default action but some other arbitrary action–much as sending electronic mail notifications–dismiss be configured.
The system comes with various pre-built filters for some of the most common services much as Apache, Courrier, SSH, FTP, Postfix and many more. Prevention is carried out by modifying the host's firewall tables. The tool can run with Netfilter, IPtables, or the hosts.deny table of TCP Wrapper. Each filter commode constitute associated with one or many another actions. Together, filters and actions are referred to as a jail.
8. AIDE
AIDE is an acronym for Advanced Trespass Sensing Environment. The free legion usurpation sleuthing system principally focuses on rootkit detective work and file signature comparisons. When you initially install AIDE, it testament compile a database of admin data from the system's configuration files. This is then used as a service line against which any change can be compared and eventually rolled back up if requisite.
Aide-de-camp uses both signature-based and anomaly-based analysis which is run on-demand and not scheduled or continuously running, This is actually this product's main drawback. However, AIDE is a command-line tool and a CRON job ass be created to run it at regular intervals. And if you run IT very oft–so much as every minute Beaver State so–you'll generate quasi-real-time information. At its Congress of Racial Equality, AIDE is goose egg just a data comparison tool. External scripts must be created to make it a true HIDS.
9. Security Onion
Security Onion is an interesting beast that can economize you very much of prison term. This is not hardly an intrusion detection or prevention system. Security Onion is a complete Linux dispersion with a focus on trespass espial, endeavor security monitoring, and backlog management. It includes many tools, few of which we've just reviewed. For instance, Security Allium cepa has Elasticsearch, Logstash, Kibana, Snort, Genus Suricata, Bro, OSSEC, Sguil, Squert, NetworkMiner, and more. All this is bundled with an easy to use setup wizard, allowing you to protect your governance within minutes. You can think of Security Onion atomic number 3 the Swiss Army knife of enterprise IT security.
The most interesting matter about this tool is that you cause everything in one simple install. And you sustain some network and host trespass detection tools. At that place are tools that use a signature-based approach and some that are anomaly-based. The distribution likewise features a combination of text-based and GUI tools. On that point's really an fantabulous mix of everything. The drawback, of run over, is that you get such that configuring it all can take out a while. But you don't have to use all the tools. You can beak solely those that you prefer.
10. Sagan
Sagan is actually more of a log analysis organisation than a true up IDS but it has some IDS-like features that we thought warranted its inclusion along our list. This tool around terminate watch the section logs of the system where it's installed but it can too interact with new tools. It could, e.g., analyze Snigger's logs, effectively adding some NIDS functionality to what is in essence a HIDS. And it won't scarcely interact with Snort. It can interact with Suricata as well and it is harmonious with various dominate building tools like Oinkmaster or Pulled Pork.
Sagan also has script execution capabilities fashioning information technology a rude intrusion bar system of rules. This instrument might not likely personify used as your sole defense against intrusion but it volition be a pregnant component of a system that can incorporate some tools by correlating events from different sources.
Conclusion
Intrusion detection systems are good one of the many tools open to atten network and system administrators in ensuring the optimal operation of their environment. Whatever of the tools discussed here are excellent only to each one has a somewhat different purpose. The one that you'll pick will largely depend happening personal preference and taxon inevitably.
Best FREE Intrusion Detection Software in 2021
Source: https://www.addictivetips.com/net-admin/intrusion-detection-tools/

0 Komentar